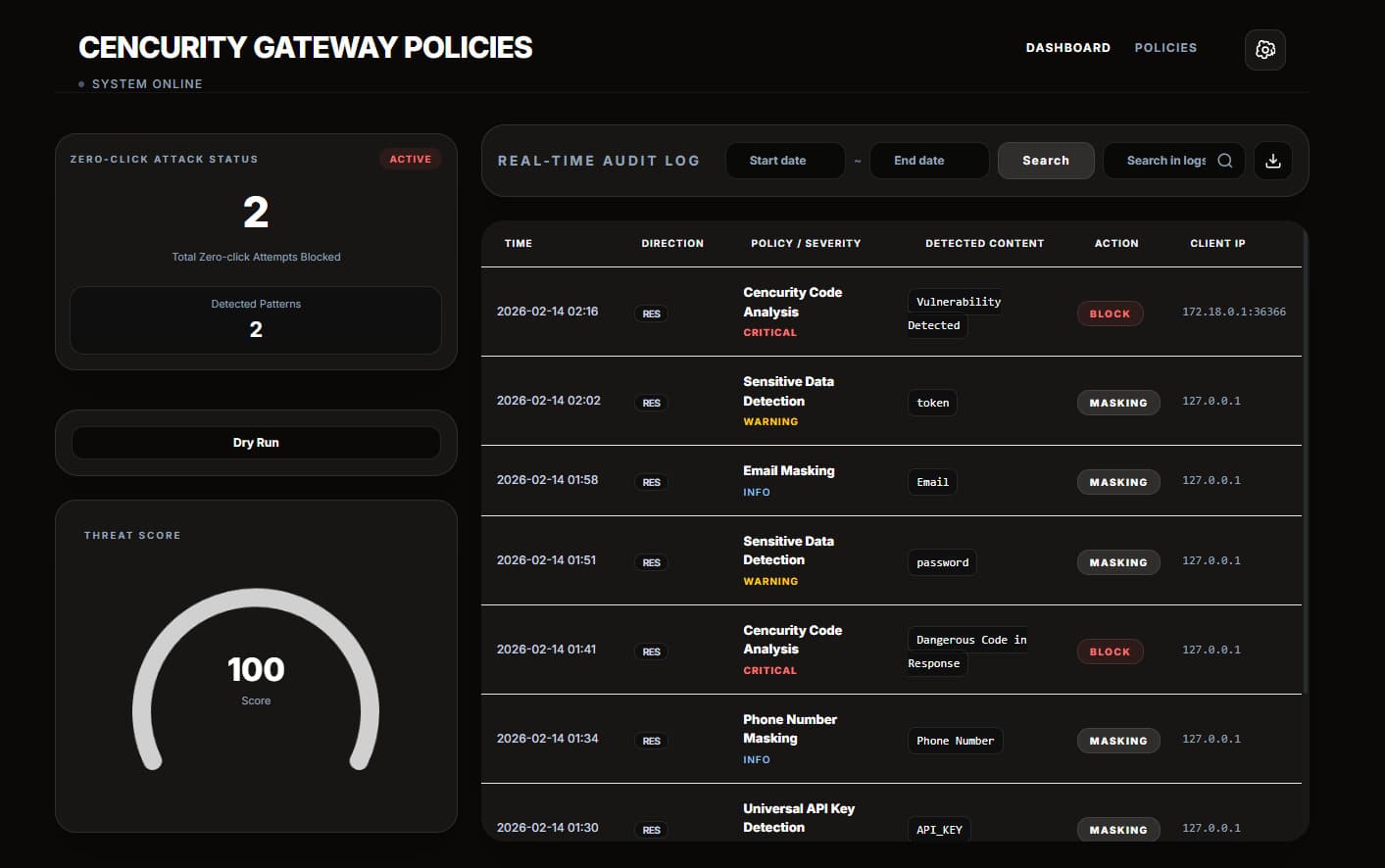
Centralized Security Dashboard
One pane of glass for every agent call—requests, responses, latency, policy hits, redactions, and blocks in real time.
No prompt leakage. No unauthorized access.
Complete security gateway for your LLM agents.

Compatible with leading AI providers—connect your existing agents and IDE workflows in minutes, without rewrites. One integration, consistent behavior across models, tools, and environments.
// What is Cencurity
One pane of glass for every agent call—requests, responses, latency, policy hits, redactions, and blocks in real time.
Stop leakage at the edge: automatically detect and block secrets, PII, and risky output before it reaches users or models.
Trace every agent interaction end-to-end. Search, filter, and correlate requests, responses, and policy decisions to pinpoint risk in seconds.
// Use cases
Personal keys. Personal access.
Issue a personal API key, sub-domain proxy URL, and dashboard per user—never shared, never reused. Dashboard access is secured exclusively by the owner’s API key,so only the key holder can access their view and credentials by default.
// Benefits
Detect policy violations fast and prioritize what matters.
Reduce risk without slowing down your delivery.
Generate clear evidence for compliance and audits.
Proxy LLM traffic and automatically redact sensitive data.
Send only verified alerts to Slack, Jira, and more.
Measure impact before enforcement, then roll out safely.
// FAQ
Common questions about demos, rollout, and operations.